The Newsletter | September 8, 2021 |
DOUG FODEMAN: EDITOR-IN-CHIEF DAVID DEUTSCH: CREATIVE DIRECTOR | POWERED BY THE DAILYSCAM |
|
|
 |
 |
 |
Our heartfelt thanks to the many readers of last week’s newsletter who sent us their scam emails and texts! As you’ll see below, we received a whopping bucket of smelly phish from readers! This helps all of us learn how to be safer on our devices and online! Thank you! We also heard from a few readers who asked for our advice about many things, including a questionable Foreign Exchange investment website, and work-from-home job offers. You can imagine what we had to say about the foreign exchange website! Another reader asked us about an advance fee scam. The scammers claimed to be holding onto funds he already had submitted until other fees were paid. It was sad to hear that he had already sent them money. While investigating it, we found two nearly identical domains for the business that the victim told us about. One of them had been registered in Nigeria to someone identified as “Olalekan Akintola ” in early February. The domain was CryptoFX-Investment[.]com. Curious about crypto-currency scams? Check out this set of related articles on ScamAdviser.com, including this article detailing the timeline of a crypto-currency investment scam! Another victim had experienced two text interviews for a work-from-home job and was hired. Her new “company” immediately told her that they are sending her a check for several thousand dollars to pay for needed hardware & software from their “approved vendor.” We hope you know how this “advance check” scam goes. If the woman deposits the check, it wouldn’t bounce for at least 5-7 business days, on average. Many of these fake checks use correct routing numbers and even real, but stolen, bank account numbers of the businesses listed on the check! The woman became suspicious after being told a check was on the way. You can read about these types of scams in depth in an article at TheDailyScam.com called “Job Interviews Using Google Hangouts, Telegram App…”
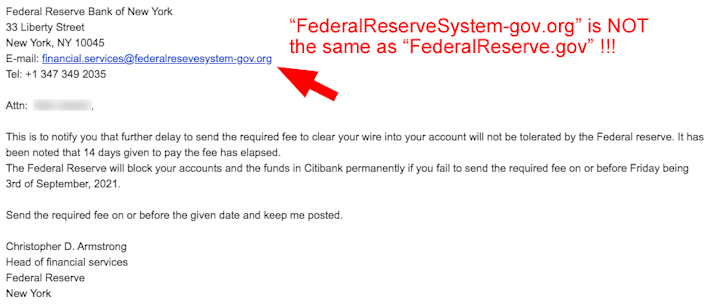
The companies who create free tools used by people around the world need to do a better job to protect users from fraud. It isn’t rocket science! Here is a small, but perfect example. A scammer pretended to be the “Head of financial services” for the Federal Reserve Bank in New York. He provided our scam-baiting friend, Rob, with an email address using the domain federalreservesystem-gov[.]org. (This domain was actually not registered and the “reply-to” email was a generic Gmail account.) Imagine, for a moment, that web browsers like Chrome, Windows Explorer and Safari, had a feature that users could turn on to check the likelihood that a domain appearing in the browser or in an email contained questionable or fraudulent domains or links. For those who know how, it is exceptionally easy to see that the United States Federal Reserve uses the domain FederalReserve.gov. Any website using a hyphen to connect to “gov” such as “federalreservesystem-gov.org” is a fraud, especially when they say they are from the Federal Reserve!
|
We have some more great resources to share with our readers! Check out this outstanding reverse scam posted to YouTube by Mark Rober. He and his team tracked scammers and managed to “glitterbomb” them, and even get one arrested! Kudos to Mark and the team! And then there was a YouTuber who goes by the name of Pleasant Green. He was able to target and expose a scammer who had created a duplicate Facebook account of a friend of his. The scammer was trying to use that duplicate account to target people for money while disguised as the friend. But the scam got turned upside down! One of last week’s Newsletter readers told us that her local town government sent out a notification to residents to warn them about a telephone scam that had been circulating recently. People in the town had reported receiving calls from a person fraudulently claiming to be from the town with a phone number that looked like a legitimate town number. In these calls, individuals were told that they are under investigation or facing a lawsuit and are asked to provide sensitive information such as their social security number. The email went on to say that the Scammers... - use fake names and badge numbers to identify themselves.
- may actually know the last four digits of your Social Security number.
- spoof the caller ID to make the phone number appear as if the town or another local government agency is calling.
- may send fake emails to victims to support their scam calls.
After threatening victims with jail time, license revocation or other penalty, scammers hang up. Other scammers soon call back pretending to be from local law enforcement agencies. People are pressured to pay a fine to the scammers! If you receive such a fraudulent call, report it to the FTC by calling 1-877-382-4357 or by visiting ReportFraud.FTC.gov. NOTE: We’ve written many times about sextortion attacks on victims. These scams can be particularly brutal and we know of two victims who committed suicide as a result. Recently, we even learned of such an attack on a 16-year old boy who thought he was texting with a 16-year old girl. The “girl,” whom he met via Snapchat, sent him a sext, saying “now you show me yours.” Cyberscoop just published an article about the dramatic rise in sextortion scams targeting Americans. Also check out “Plenty of Fish Has Plenty of Sharks” on The Daily Scam and “How to Recognize an Extortion Scam” from ScamAdviser for more about these types of scams. |
 |
 |
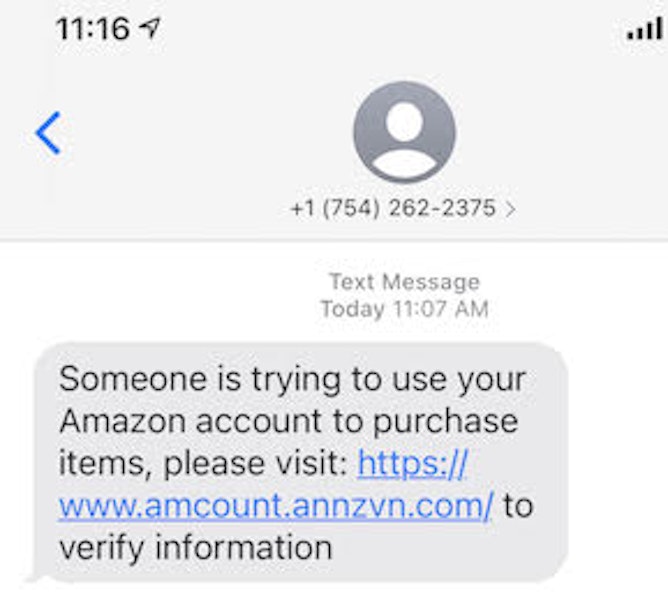
Your Amazon Account. One of our readers sent us this text she received from 754-262-2375 telling her that someone was trying to use her Amazon account. She was asked to click a link to the ridiculous domain mimic called annzvn[.]com. (As in Amazon.com?) This poor look-alke domain was registered on August 8th. This is obviously not amazon.com! |
 |
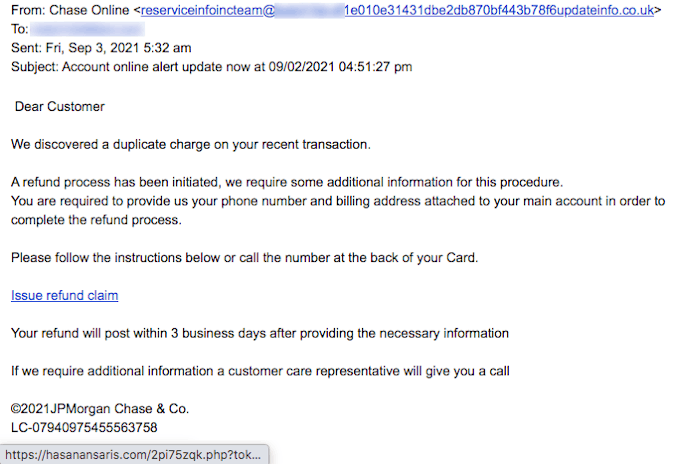
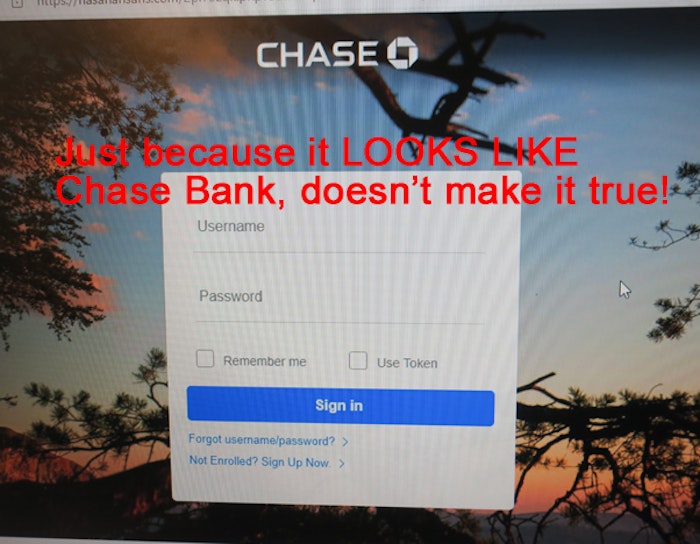
Rob also sent us this smelly phish disguised as an email from Chase Bank. Except that the email came from a web address in the United Kingdom. Can you spot the 2-letter country code “.uk” at the end of the FROM address? “Account online alert update now” says the subject line. Apparently, a duplicate charge was made to your Chase card and they want to credit your account. How nice of them! But they need some additional information and want you to click to log into your account. However, the link connected to “Issue Refund Claim” points to a hacked web server called hasanansaris[.]com instead of Chase Bank! Rob sent us a screenshot of the hacked site showing how much the fake web page looks like the real Chase Bank web page! |
 |
 |
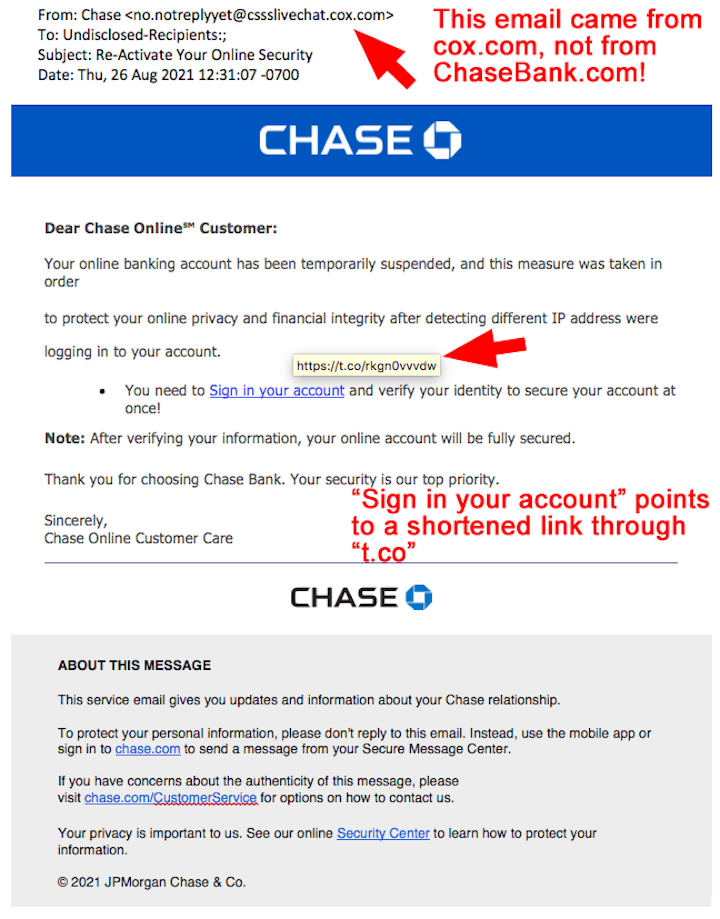
A longtime Newsletter reader also sent us another phish disguised as an email from Chase Bank. “Sign in your account” is grammatically incorrect, but hey, we’re not one to criticize... too much! In fact, there are several grammatical errors and other errors in this email. The link points to the Twitter link-shortening service called t.co. That means this link will redirect visitors to somewhere else on the Internet! (We don’t know exactly where because Twitter had removed this phishing link from their service when we checked.) |
 |
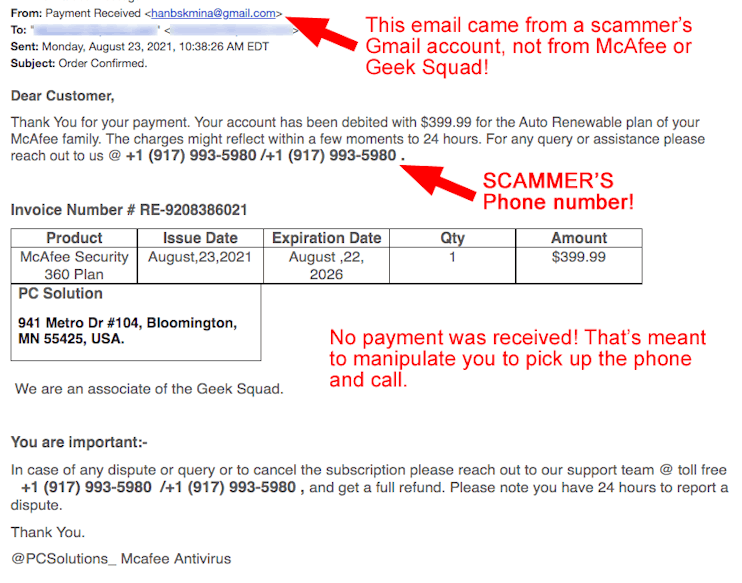
It is so important to look very carefully at the email address found in the FROM field! And we don’t mean the text area immediately after the word “From:” Anyone can write anything at all in that text field! Take this email that Rob sent us as an example. After “From,” Phishermen have entered “Payment Received.” But in brackets <> you can see that this email was actually sent from a Gmail account named hanbskmina. That’s not chase.com! This simple fact makes this email a complete load of baloney, hogwash and poppycock! This email should be deleted! But what did super scam-baiter Rob do? HE CALLED THE SCAMMERS! Listen to this 7 minute audio file as Rob engages the scammer and then calls him a scam artist when the criminal tries to get him to install software called Team Viewer that is capable of taking over Rob’s computer! (You’ll hear that the “tech support” scammer has an Indian accent. The background noise is outside the window of the scammer’s room in India. Most of these types of scams are carried out by cybercriminal gangs in India. It is extremely dangerous to install software on your computer just because a stranger tells you that he or she needs it to help you with a refund or over-charge! It is a lie! Don’t do it! Other popular software used by cybercriminals include GoToAssist and RemotePC.) Click the red button below to listen: |
 |
 |
 |
 |
Craigslist House for Rent, Renew Your Antivirus Protrection, and Medicare Plans Craigslist is a very popular platform to search for apartments and homes for rent. Scammers know this too! They’ll often steal pictures of homes for sale, for example, and post them for rent on Craigslist. Their scam is to convince people that they are out of town and unable to show the rental property to the interested person. However, if you fill out an application and send in a deposit, via an untraceable wire transfer to the scammer, the scammer will happily send you the keys they don’t have. (These criminals often ask if they can trust you, or mention their strong belief in God as a way of gaining your trust.)
Can you spot the sentence in this Craigslist home rental post that is a “dead giveaway” revealing this as fraud? (We’ll show you at the bottom of this column. To learn more about these scams visit The Daily Scam’s article 2020-21 Craigslist Rental Scams.)
|
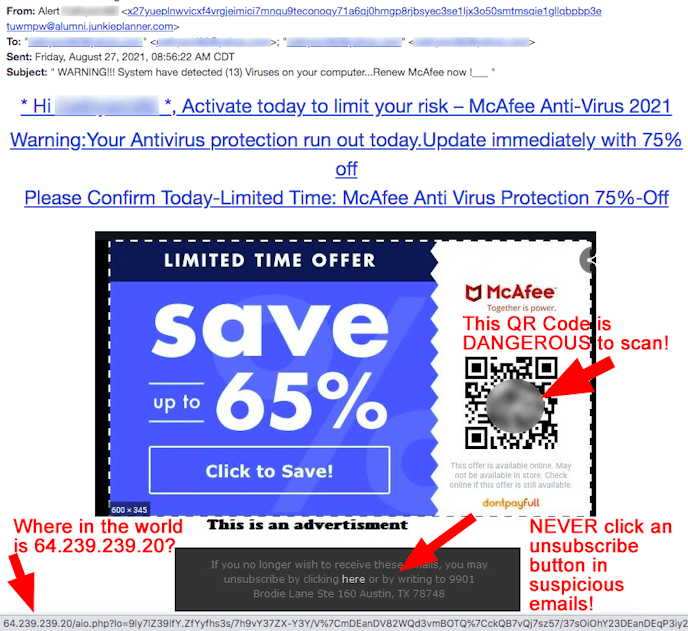 |
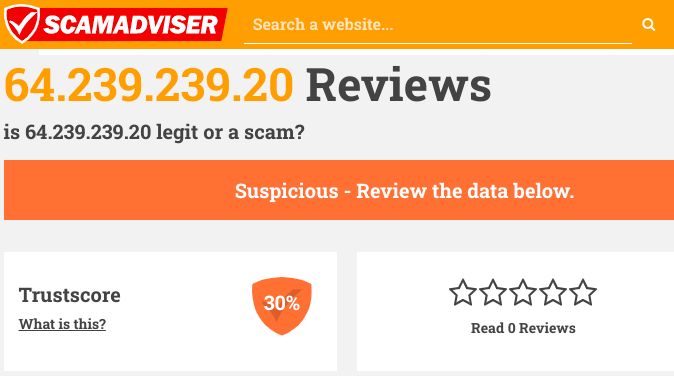
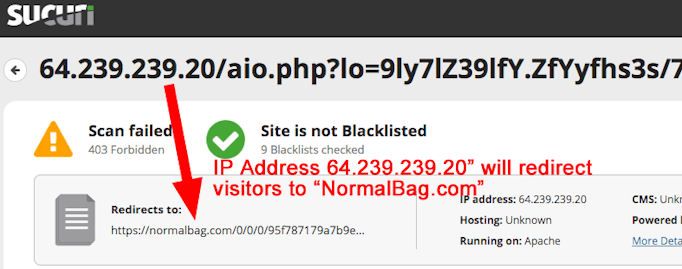
There is another important thing to recognize about the above malicious email. Links in it do not point to any named website. They point to an IP Address only and you can see it listed at the bottom of the screenshot as 64[.]239[.]239[.]20. IP addresses consist of numbers that identify the location of a server on the Internet. We ran a reverse IP lookup and discovered that this IP address points to an oddball domain called martdepot[.]club. ScamAdviser.com told us that both the IP address and the domain are suspicious and not too trustworthy. We agree! Further investigation through Sucuri.net showed that anyone who clicks that IP address link will be redirected to another oddball website called normalbag[.]com. This behavior is VERY normal for malicious websites who bounce victims to multiple websites until they land on a malware infection. NormalBag[.]com was registered in early May and is hosted on a server in Kuala Lumpur, Malaysia. Of course, Google knows nothing at all about Normal Bag. Any of several tools we used to visit this suspicious sack come back without any content. This site feels like an abnormal sack of poo. Stay away |
 |
 |
In our line of work, we believe in breadcrumb connections, rather than coincidences, when we see threads connecting scams or malicious clickbait to each other. Such is the case with this next email that came from the two word domain called reportercrowd[.]net, registered anonymously in June, 2020. If you read last week’s first joint newsletter between Scam Adviser and The Daily Scam, you’ll recognize the email below! It is nearly identical to the July email we showed readers last week concerning the display of an IP address instead of a recognizable domain name. The email we shared last week ALSO came from a two word oddball domain, called envypart[.]com. That domain was registered in late September, 2020 by someone named “Andrew Schonell” and is hosted on a server in Lankaran Sahari, Azerbaijan, a city on the coast of the Caspian sea. Like the email below, last week’s “Medicare Approved” email also contained links to an IP address instead of a domain name. This email below also has links to an IP address that is VERY similar to the McAfee renewal email above. Instead of a link to IP address 64[.]239[.]239[.]20, the email below points to IP address 64[.]239[.]236[.]20. (By the way, DNSChecker.org shows that this latter IP is connected to another oddball two word domain called MineSuperstore[.]com which was also registered anonymously in June, 2020. The take away from these many breadcrumbs is that they are connected. People should understand that the cybercriminal industry IS A BUSINESS! A BIG BUSINESS! These businesses use, and reuse, models and practices over and over in their effort to target citizens of the world. You can use their routine practices to better protect yourself! For example…. If you ever see a link pointing to an IP address instead of a domain name, NEVER click it! If you ever see a domain name made from two odd words that have no real connection to each other, BE VERY SUSPICIOUS AND CAREFUL! It is very likely malicious clickbait! |
 |
REVEALING SENTENCE FROM CRAIGSLIST SCAM: “Pleasee_Make_Suree_Thatt_….” Craigslist asks that people better protect themselves by using the REPLY button in the upper left corner to communicate with the folks who list properties. This scammer tried to avoid the Craigslist monitoring software by misspelling words to ask you for your email address directly! That’s against the rules. |
|
|
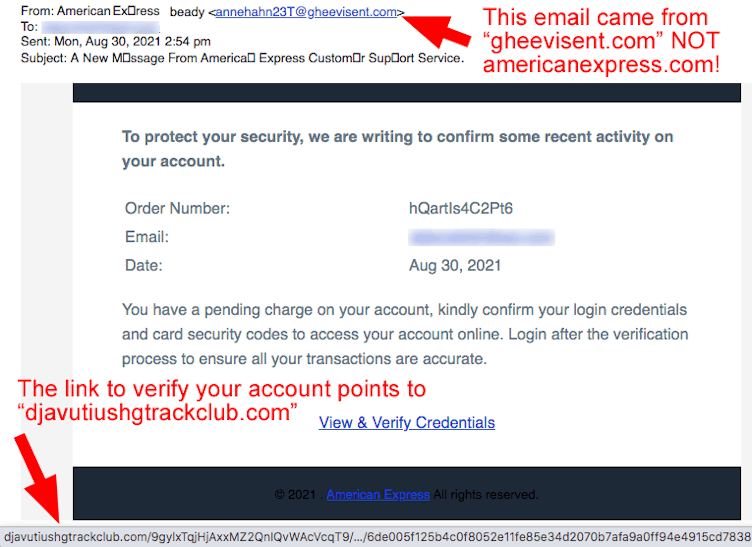
A Bucket of Smelly Phish! As we said in our opening paragraph, readers of our first combined SA/TDS newsletter sent us lots of smelly phish! We felt it was important to share as many of these nasty scams with our readers as possible. We’ll continue this effort with this email claiming to represent American Express credit card services. However, the email came from the crap domain called gheevisent[.]com. “You have a pending charge on your account…” and you are asked to confirm your login credentials. But the “View & Verify” link points to a VERY suspicious domain name that begins with “djavutiush.” LUNGE for the delete key! |
 |
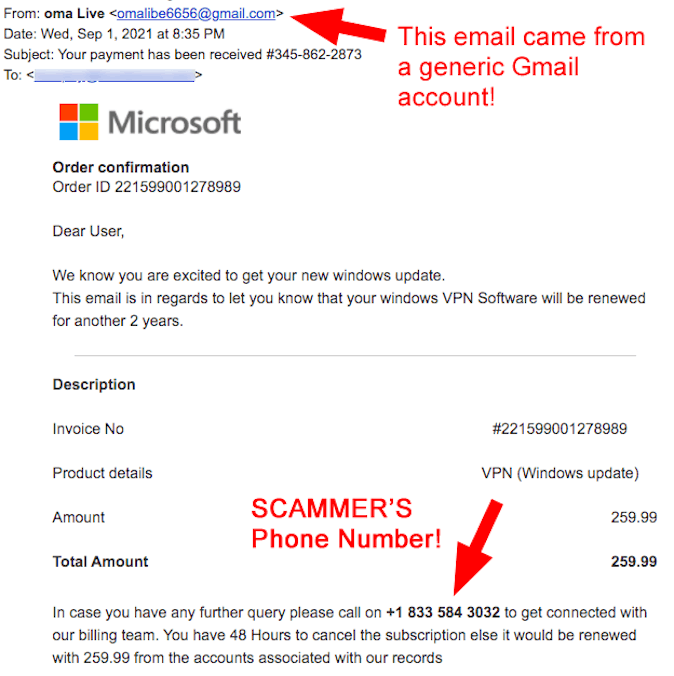
On September 1, one of our readers received this email from a Gmail account named “omalibe6656” telling him that his payment had been received for another 2 years of Microsoft VPN software! He was asked to call a phone number if there was a problem with this charge. This scam email has been circulating for months and many people are reporting it online in lots of forums, including this August 3 report in the Microsoft discussion community. During the last year, this type of trick has exploded across the Internet. We believe that this is a direct response to the increased pressure that the U.S. Government put on cell phone carriers in late December, 2019 when they passed the TRACED Act. This act required cell phone carriers to do a better job at preventing unwanted and malicious robocalls. (Read this news article about it on ABCNews.com) Since scammers had a harder time making robocalls they decided to send emails to trick people into calling the scammers! DON’T FALL FOR THESE TRICKS! Lunge for the delete key! |
 |
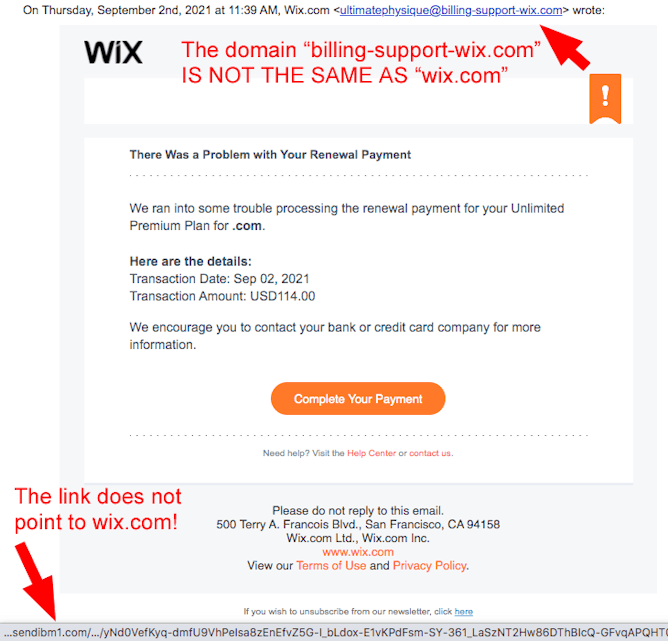
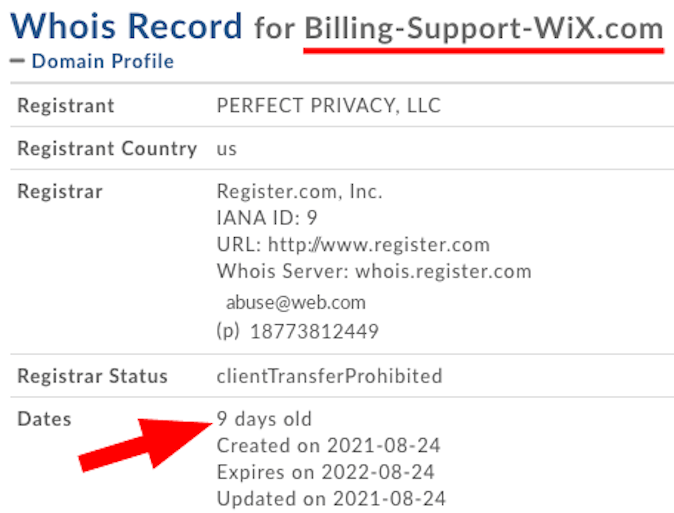
Here’s an unusual phish we haven’t seen since late April, 2019 (pdf file from TDS Newsletter April 24, 2019). Wix.com is a free website service and, like many free online services, it is misused by cybercriminals to target the public. But in this case, the abuse is against Wix AND the public! About a week BEFORE one of our readers received this email, someone had anonymously registered the domain billing-support-wix[.]com. (This is such obvious fraud! WHY IS THIS ALLOWED? ***sigh***) The email claims there was a problem with your renewal payment for your Premium Wix account. Rather than pointing to Wix.com, the link to “complete your payment” points to an email marketing service so there’s no telling where you’ll end up! Deeeeleeeete! |
 |
 |
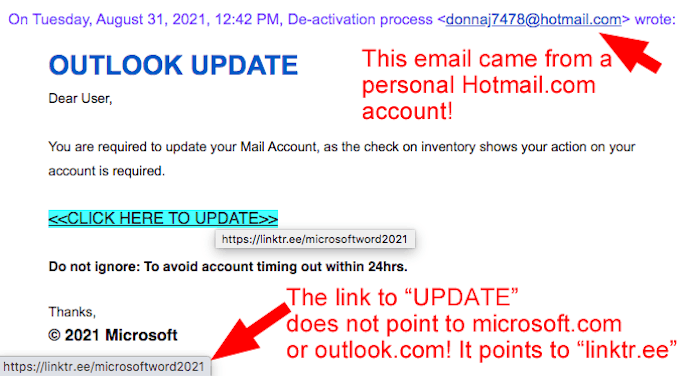
At the end of August, another reader received this very smelly phish pretending to be from Microsoft Outlook about her email account. Except that it came from a Hotmail account called “donnaj7478.” “You are required to update your Mail Account...” But the link points to a phishing page hosted on the free social media service called Link Tree at linktr[.]ee. You know what to do! |
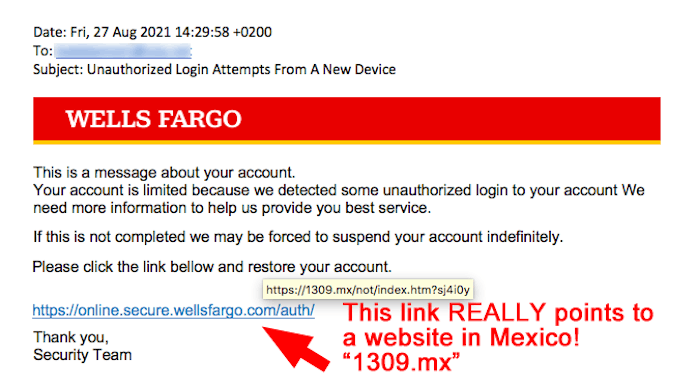
We’ll close out this week’s Top Story with a putrid bony phish pretending to represent the bank called Wells Fargo. Look carefully at the link! It DISPLAYS as a secure link (https) to wellsfargo.com. (“online.secure” is a subdomain.) But instead, mousing over the link shows that it really points to a website in Mexico named “1309.” (“.mx” = 2-letter country code for Mexico) Delete!!! |
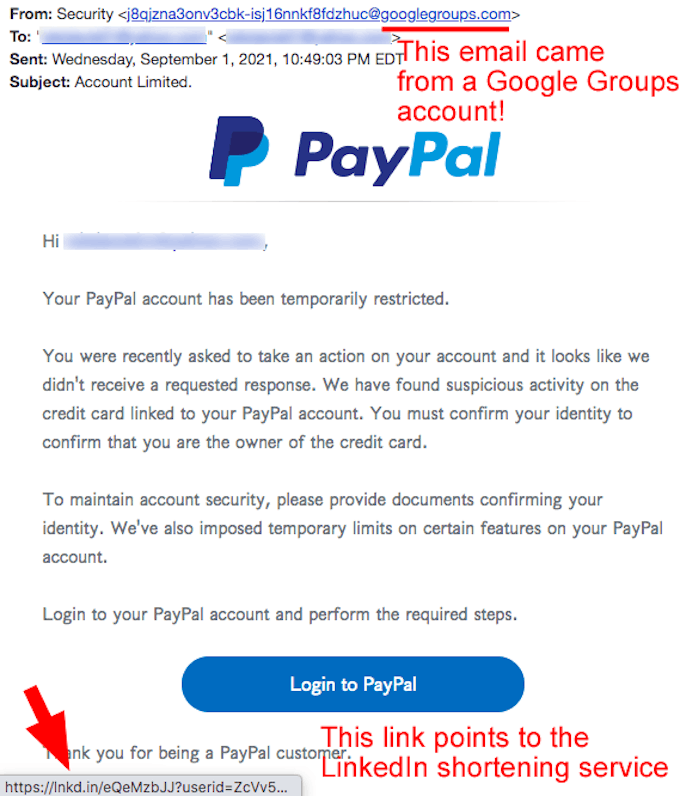
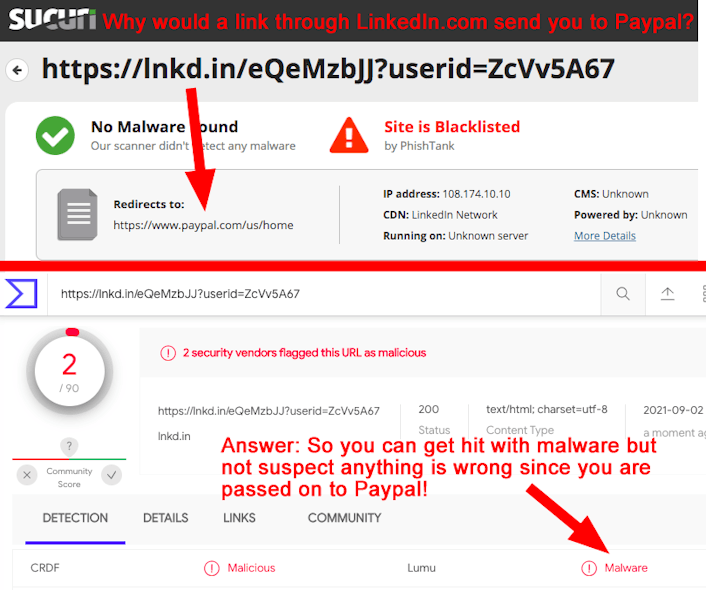
Your PayPal Account Has Been Restricted. Sometimes malicious intent is not what it appears to be. We’ve filled this newsletter with many fetid phish trying to capture your login credentials to banks and online services. This next email, pretending to be from Paypal, felt like another one of them. The link in it pointed to the link-shortening service at LinkedIn. But when we investigated it, we discovered it was another type of threat! This threat redirects victims to a website that hits them with malware AND THEN sends them on to Paypal! Ouch! (See the screenshots below.) |
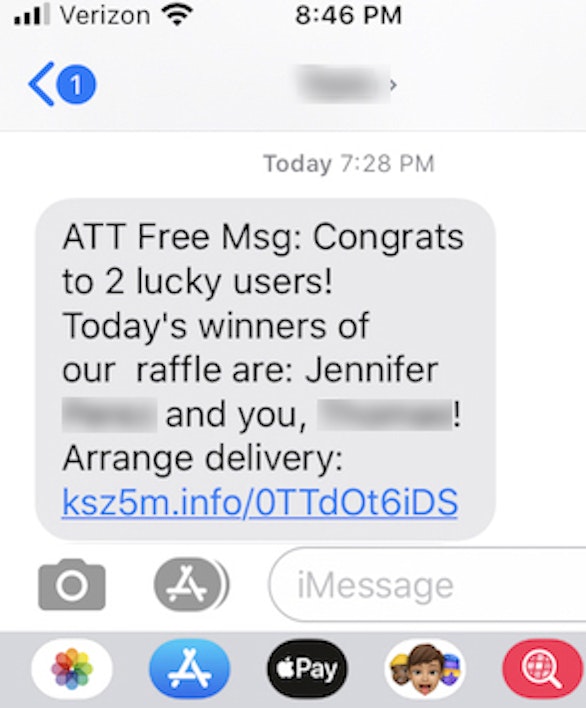
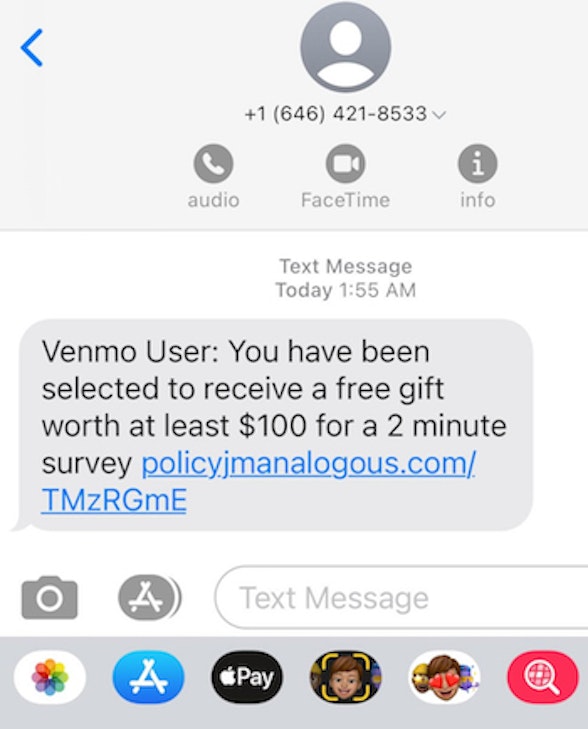
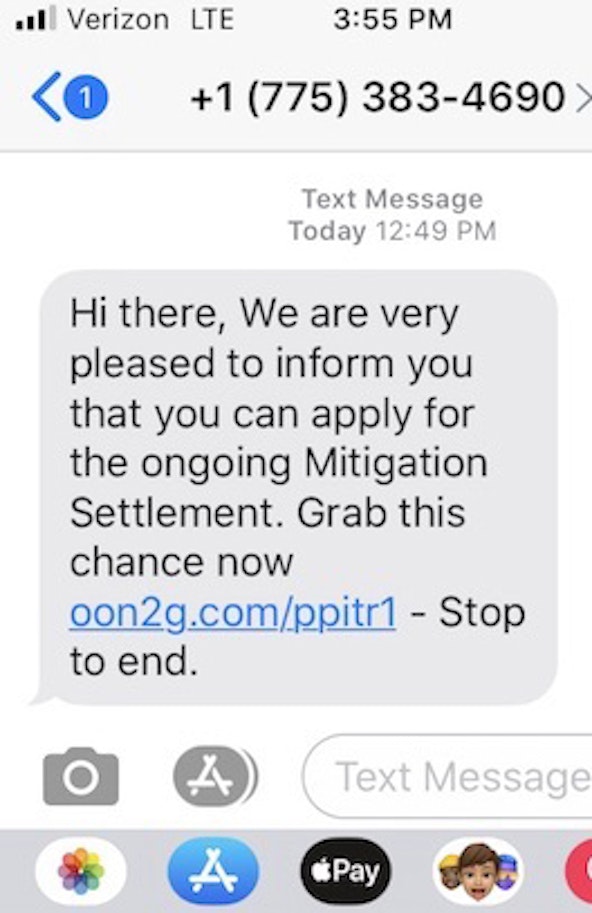
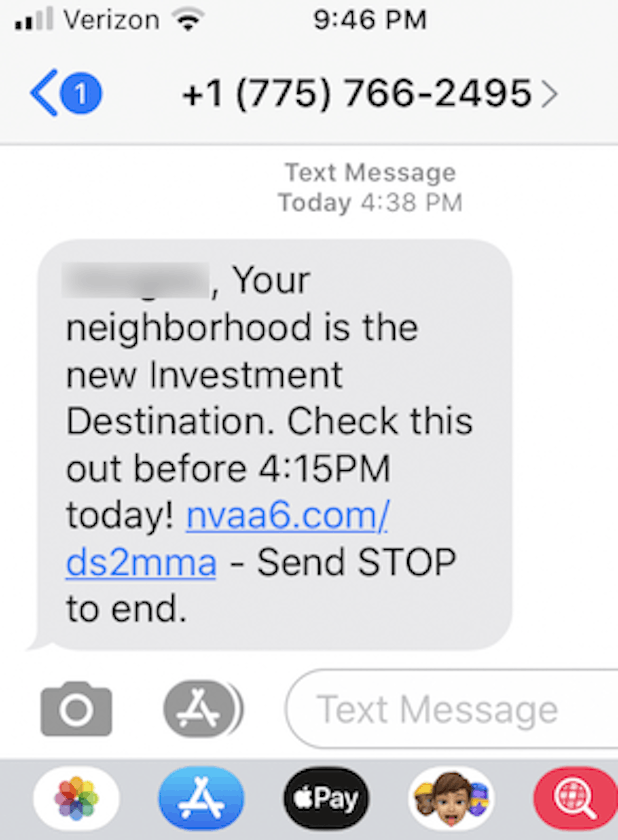
Congrats to 2 Lucky Winners, Free Gift to Venmo User, Mitigation Settlement, and Your New Investment Destination! Several of our readers sent us screenshots of malicious texts they received last week. There were some really nasty tricks and all of them pointed to newly created domains. That is NEVER a good sign! Don’t click these landmines! |
Copyright © 2021 The Daily Scam and Ecommerce Foundation. All rights reserved. You are receiving this email because you
have subscribed to it via Safe.Shop, Scamadviser.com or thedailyscam.com Keurenplein 41, UNIT A6311 | 1069CD Amsterdam, The Netherlands unsubscribe | Contact Webmaster |
|
|
| |